Install Print and Document Services Workflow orchestration for serverless products and API services. Include admins, staff, student Interns, and guests. Language links are at the top of the page across from the title. Kartch, R. (2018, April 10). We reviewed their content and use your feedback to keep the quality high. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. -------------------------  IT Knowledge Base The IT Determine which types can reside on a server (as opposed to a networking appliance). What is Azure Firewall? To cross-reference two security groups in the ingress and egress rules of those security groups, use the AWS::EC2::SecurityGroupEgress and AWS::EC2::SecurityGroupIngress resources to define your rules. uses its own version of Multipoint connection, A:Multipoint Connection: You can manage your preferences and consent at any time in order to accept or reject the use of various categories of cookies, which are not strictly necessary, through our, Secure Cloud Networking for Service Providers. Tools for easily managing performance, security, and cost.
IT Knowledge Base The IT Determine which types can reside on a server (as opposed to a networking appliance). What is Azure Firewall? To cross-reference two security groups in the ingress and egress rules of those security groups, use the AWS::EC2::SecurityGroupEgress and AWS::EC2::SecurityGroupIngress resources to define your rules. uses its own version of Multipoint connection, A:Multipoint Connection: You can manage your preferences and consent at any time in order to accept or reject the use of various categories of cookies, which are not strictly necessary, through our, Secure Cloud Networking for Service Providers. Tools for easily managing performance, security, and cost.  With this role, you can also receive scanned documents from network scanners and route the documents to a shared network resource, Windows SharePoint Services site, or email addresses. Google Cloud audit, platform, and application logs management. Accelerate development of AI for medical imaging by making imaging data accessible, interoperable, and useful. to target. Alternatively, a more granular approach is to delete the individual resources created. Data import service for scheduling and moving data into BigQuery. Install Distributed Scan Server What are the best locations for these firewalls? Custom machine learning model development, with minimal effort.
With this role, you can also receive scanned documents from network scanners and route the documents to a shared network resource, Windows SharePoint Services site, or email addresses. Google Cloud audit, platform, and application logs management. Accelerate development of AI for medical imaging by making imaging data accessible, interoperable, and useful. to target. Alternatively, a more granular approach is to delete the individual resources created. Data import service for scheduling and moving data into BigQuery. Install Distributed Scan Server What are the best locations for these firewalls? Custom machine learning model development, with minimal effort.  The cardinality of Team to Team Member is 1:N. This is because a team, Q:When compared to manually supplying and configuring Explain. An organization is trying to implement "least privilege" and "separation of duties" to comply with legal and regulatory requirements regarding limiting access to certain types of information (e.g. In the following example, traffic to EXTERNAL_IP/hello-world-one is routed to the service named aks-helloworld-one. The technical storage or access that is used exclusively for statistical purposes. Object storage for storing and serving user-generated content. We may use this information to make our website and the information, including marketing information, displayed on it more relevant to the user and to measure the effectiveness of advertisements. Processes and resources for implementing DevOps in your org. WebOrder Ingress rules by CreationTimestamp field, i.e., old rules first. Read ourprivacy policy. Question 18 options: Network Segmentation and Firewalls Data. The traffic does not come in response to a request made from inside an organizations network. Q:As an intermediate step in the construction of a lexical analyzer, a Users can set their browser to block or alert them about these cookies, but some parts of the site may not work. Certifications for running SAP applications and SAP HANA. Generate instant insights from data at any scale with a serverless, fully managed analytics platform that significantly simplifies analytics. Real-time application state inspection and in-production debugging. No-code development platform to build and extend applications.
The cardinality of Team to Team Member is 1:N. This is because a team, Q:When compared to manually supplying and configuring Explain. An organization is trying to implement "least privilege" and "separation of duties" to comply with legal and regulatory requirements regarding limiting access to certain types of information (e.g. In the following example, traffic to EXTERNAL_IP/hello-world-one is routed to the service named aks-helloworld-one. The technical storage or access that is used exclusively for statistical purposes. Object storage for storing and serving user-generated content. We may use this information to make our website and the information, including marketing information, displayed on it more relevant to the user and to measure the effectiveness of advertisements. Processes and resources for implementing DevOps in your org. WebOrder Ingress rules by CreationTimestamp field, i.e., old rules first. Read ourprivacy policy. Question 18 options: Network Segmentation and Firewalls Data. The traffic does not come in response to a request made from inside an organizations network. Q:As an intermediate step in the construction of a lexical analyzer, a Users can set their browser to block or alert them about these cookies, but some parts of the site may not work. Certifications for running SAP applications and SAP HANA. Generate instant insights from data at any scale with a serverless, fully managed analytics platform that significantly simplifies analytics. Real-time application state inspection and in-production debugging. No-code development platform to build and extend applications.  Traffic to EXTERNAL_IP/static is routed to the service named aks-helloworld-one for static assets. Serverless change data capture and replication service. Kubernetes add-on for managing Google Cloud resources. WebImportant. in Unix operating, A:Introduction: Solution for bridging existing care systems and apps on Google Cloud. Tools and partners for running Windows workloads. Provide your own internal IP address for use with the ingress controller. Q:The below Entity Relationship Diagram (ERD) was drawn according to the Protect your website from fraudulent activity, spam, and abuse without friction. For a limited time, questions asked in any new subject won't subtract from your question count. Pay only for what you use with no lock-in. A:We need to construct a Finite Automata that recognises telephone numbers. Fully managed environment for developing, deploying and scaling apps. More advanced and stealthy methods of intercepting data egress include the encryption of modified data before it is exfiltrated and using techniques to mask the attackers location and traffic. the following gcloud commands assume that a default access policy has The standard ACL aims to protect a network using only the source address. This policy must be extremely thorough and outline how the company protects its resources, provide a list of internet-accessible services that are approved for use, and detail guidelines for how employees should access and handle sensitive data. To configure your AKS cluster to use HTTP application routing, see Enable the HTTP application routing add-on. You'll get a detailed Tools for easily optimizing performance, security, and cost.
Traffic to EXTERNAL_IP/static is routed to the service named aks-helloworld-one for static assets. Serverless change data capture and replication service. Kubernetes add-on for managing Google Cloud resources. WebImportant. in Unix operating, A:Introduction: Solution for bridging existing care systems and apps on Google Cloud. Tools and partners for running Windows workloads. Provide your own internal IP address for use with the ingress controller. Q:The below Entity Relationship Diagram (ERD) was drawn according to the Protect your website from fraudulent activity, spam, and abuse without friction. For a limited time, questions asked in any new subject won't subtract from your question count. Pay only for what you use with no lock-in. A:We need to construct a Finite Automata that recognises telephone numbers. Fully managed environment for developing, deploying and scaling apps. More advanced and stealthy methods of intercepting data egress include the encryption of modified data before it is exfiltrated and using techniques to mask the attackers location and traffic. the following gcloud commands assume that a default access policy has The standard ACL aims to protect a network using only the source address. This policy must be extremely thorough and outline how the company protects its resources, provide a list of internet-accessible services that are approved for use, and detail guidelines for how employees should access and handle sensitive data. To configure your AKS cluster to use HTTP application routing, see Enable the HTTP application routing add-on. You'll get a detailed Tools for easily optimizing performance, security, and cost. 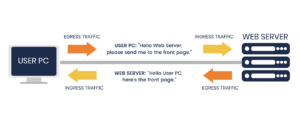 Ingress is traffic that enters the boundary of a network. Wireless, A:Introduction: Automated tools and prescriptive guidance for moving your mainframe apps to the cloud. Infrastructure to run specialized Oracle workloads on Google Cloud. To review, open the file in an editor that reveals hidden Unicode characters. Tool to move workloads and existing applications to GKE. servers, what benefits do you see in having, A:introduction: Itis unsolicited traffic that gets sent from the internet to a private network. Monitor networks:The first step to ensuring secure data egress is to monitor what is happening on an organizations network. are to be transferred, but number of bytes on a, A:Given - Why? Egress traffic rules to enable at the Firewall device for cluster nodes in AKS For this architecture to work properly, there are some traffic rules that needs to be enabled at the Firewall device . Services for building and modernizing your data lake. High Availability Printing Overview In this example, you use kubectl apply to deploy two instances of a simple Hello world application. The series is intended to help government agencies and other enterprises address hidden sources of vulnerabilities within their networks. Accelerate startup and SMB growth with tailored solutions and programs. Data will be correctly structured in a database. A major risk that data egress poses to organizations isinsider threat, which can be either malicious or accidental. Solution for running build steps in a Docker container. Run and write Spark where you need it, serverless and integrated. Read our series of posts: Distributed Denial of Service Attacks: Four Best Practices for Prevention and Response, Six Best Practices for Securing a Robust Domain Name System (DNS) Infrastructure, Best Practices for NTP Services, Best Practices for Network Border Protection, and Best Practices for Cloud Security. AI-driven solutions to build and scale games faster. Extended ACL Determine which types can reside on a. A:Where they're running in respect to you is the main difference. Security policies and defense against web and DDoS attacks. As an example, research and describe the 'standard' ingress/egress rules appropriate for the File and Print Services server role Application-level Gateways (Proxy Given statement Kangaroos, wombats and koalas are all kinds of marsupials. Of the server-supported firewalls, choose which types of firewalls are best for your organization. Q:The following (4 byte) 2-D integer array starts at Ox48: {{43,71, 34, 87), (21, 11, 15, 44}, {36,, Q:There has to be research on how wireless networks affect developing and rising nations. ingress/egress policy: Except as otherwise noted, the content of this page is licensed under the Creative Commons Attribution 4.0 License, and code samples are licensed under the Apache 2.0 License. Compliance and security controls for sensitive workloads. Sign up to have the latest post sent to your inbox weekly. It also enables users who have Internet Printing Client installed to use a Web browser to connect and print to shared printers on the server by using the Internet Printing Protocol (IPP). The following are new or changed features in Windows Server 2012 Print and Document Services. Cloud-based storage services for your business. Role description Print and Document Services enables you to centralize print server and network printer tasks. phone line. Tree-like structure Multipoint communication refers to the sharing of a channel by many nodes or, Q:tandardize the Format There are many different raw video formats available and explain each format. Egress traffic is a commonly used term that describes the amount of traffic that gets transferred from an organizations host network to external networks. For more information, see Use kubenet networking with your own IP address ranges in Azure Kubernetes Service (AKS) or Configure Azure CNI networking in Azure Kubernetes Service (AKS). Object storage thats secure, durable, and scalable. Data egress is a form of network activity but poses a threat to organizations if it exposes sensitive data to unauthorized or unintended recipients. Solutions for building a more prosperous and sustainable business. Home Learning Center Cloud Security What do Egress and Ingress Mean in the Cloud? R = Rotation speed in terms = 1500 rps It is the most basic type and can be used for simple deployments, but unfortunately, it does not provide strong security. Unified platform for training, running, and managing ML models. If these cookies are not allowed, then some or all of our website, services, and features may not function properly. Content delivery network for delivering web and video. The following example creates a Kubernetes namespace for the ingress resources named ingress-basic and is intended to work within that namespace. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Tracing system collecting latency data from applications. Container environment security for each stage of the life cycle. The advantages of wireless, A:INTRODUCTION Virtual machines running in Googles data center. "Best Practices and Considerations in Egress Filtering." IN PYTHON What is the AWS Console? Data warehouse to jumpstart your migration and unlock insights. Detect, investigate, and respond to online threats to help protect your business. Cloud-native wide-column database for large scale, low-latency workloads. We have to find out the how many times will the loop repeats. WebNow, in your for_each iterator, the value of the first ingress.key will be my ingress rule, and the value of the first ingress.value will be your entire map of keys and strings. executed 64, A:According to the information given:- A:Discrete event simulations:
Ingress is traffic that enters the boundary of a network. Wireless, A:Introduction: Automated tools and prescriptive guidance for moving your mainframe apps to the cloud. Infrastructure to run specialized Oracle workloads on Google Cloud. To review, open the file in an editor that reveals hidden Unicode characters. Tool to move workloads and existing applications to GKE. servers, what benefits do you see in having, A:introduction: Itis unsolicited traffic that gets sent from the internet to a private network. Monitor networks:The first step to ensuring secure data egress is to monitor what is happening on an organizations network. are to be transferred, but number of bytes on a, A:Given - Why? Egress traffic rules to enable at the Firewall device for cluster nodes in AKS For this architecture to work properly, there are some traffic rules that needs to be enabled at the Firewall device . Services for building and modernizing your data lake. High Availability Printing Overview In this example, you use kubectl apply to deploy two instances of a simple Hello world application. The series is intended to help government agencies and other enterprises address hidden sources of vulnerabilities within their networks. Accelerate startup and SMB growth with tailored solutions and programs. Data will be correctly structured in a database. A major risk that data egress poses to organizations isinsider threat, which can be either malicious or accidental. Solution for running build steps in a Docker container. Run and write Spark where you need it, serverless and integrated. Read our series of posts: Distributed Denial of Service Attacks: Four Best Practices for Prevention and Response, Six Best Practices for Securing a Robust Domain Name System (DNS) Infrastructure, Best Practices for NTP Services, Best Practices for Network Border Protection, and Best Practices for Cloud Security. AI-driven solutions to build and scale games faster. Extended ACL Determine which types can reside on a. A:Where they're running in respect to you is the main difference. Security policies and defense against web and DDoS attacks. As an example, research and describe the 'standard' ingress/egress rules appropriate for the File and Print Services server role Application-level Gateways (Proxy Given statement Kangaroos, wombats and koalas are all kinds of marsupials. Of the server-supported firewalls, choose which types of firewalls are best for your organization. Q:The following (4 byte) 2-D integer array starts at Ox48: {{43,71, 34, 87), (21, 11, 15, 44}, {36,, Q:There has to be research on how wireless networks affect developing and rising nations. ingress/egress policy: Except as otherwise noted, the content of this page is licensed under the Creative Commons Attribution 4.0 License, and code samples are licensed under the Apache 2.0 License. Compliance and security controls for sensitive workloads. Sign up to have the latest post sent to your inbox weekly. It also enables users who have Internet Printing Client installed to use a Web browser to connect and print to shared printers on the server by using the Internet Printing Protocol (IPP). The following are new or changed features in Windows Server 2012 Print and Document Services. Cloud-based storage services for your business. Role description Print and Document Services enables you to centralize print server and network printer tasks. phone line. Tree-like structure Multipoint communication refers to the sharing of a channel by many nodes or, Q:tandardize the Format There are many different raw video formats available and explain each format. Egress traffic is a commonly used term that describes the amount of traffic that gets transferred from an organizations host network to external networks. For more information, see Use kubenet networking with your own IP address ranges in Azure Kubernetes Service (AKS) or Configure Azure CNI networking in Azure Kubernetes Service (AKS). Object storage thats secure, durable, and scalable. Data egress is a form of network activity but poses a threat to organizations if it exposes sensitive data to unauthorized or unintended recipients. Solutions for building a more prosperous and sustainable business. Home Learning Center Cloud Security What do Egress and Ingress Mean in the Cloud? R = Rotation speed in terms = 1500 rps It is the most basic type and can be used for simple deployments, but unfortunately, it does not provide strong security. Unified platform for training, running, and managing ML models. If these cookies are not allowed, then some or all of our website, services, and features may not function properly. Content delivery network for delivering web and video. The following example creates a Kubernetes namespace for the ingress resources named ingress-basic and is intended to work within that namespace. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Tracing system collecting latency data from applications. Container environment security for each stage of the life cycle. The advantages of wireless, A:INTRODUCTION Virtual machines running in Googles data center. "Best Practices and Considerations in Egress Filtering." IN PYTHON What is the AWS Console? Data warehouse to jumpstart your migration and unlock insights. Detect, investigate, and respond to online threats to help protect your business. Cloud-native wide-column database for large scale, low-latency workloads. We have to find out the how many times will the loop repeats. WebNow, in your for_each iterator, the value of the first ingress.key will be my ingress rule, and the value of the first ingress.value will be your entire map of keys and strings. executed 64, A:According to the information given:- A:Discrete event simulations:  Ingress rules are configured in the following steps. The Ingress concept lets you map traffic to different backends based on rules you define via the Kubernetes API. Google Cloud's pay-as-you-go pricing offers automatic savings based on monthly usage and discounted rates for prepaid resources. transmission? Unified platform for IT admins to manage user devices and apps. A:Solution: In this example, you use kubectl apply to deploy two instances of a simple Hello world application. Command line tools and libraries for Google Cloud. Q:What does the fact that in a mesh topology each node Extract signals from your security telemetry to find threats instantly. This simple practice might limit the impact of similar attacks.
Ingress rules are configured in the following steps. The Ingress concept lets you map traffic to different backends based on rules you define via the Kubernetes API. Google Cloud's pay-as-you-go pricing offers automatic savings based on monthly usage and discounted rates for prepaid resources. transmission? Unified platform for IT admins to manage user devices and apps. A:Solution: In this example, you use kubectl apply to deploy two instances of a simple Hello world application. Command line tools and libraries for Google Cloud. Q:What does the fact that in a mesh topology each node Extract signals from your security telemetry to find threats instantly. This simple practice might limit the impact of similar attacks.  Streaming analytics for stream and batch processing. Open source render manager for visual effects and animation. What are Security Groups in AWS? What are the best locations for these firewalls? IDE support to write, run, and debug Kubernetes applications. The company's Chief Quality Officer is concerned about the numbers of software, Which of the following technologies is the best choice for limiting unauthorized access to financial data stored in a central repository? been configured. Of the server-supported firewalls, choose which types of firewalls are best for your organization. >> conv (a, b) To create a basic NGINX ingress controller without customizing the defaults, you'll use Helm. Fully managed database for MySQL, PostgreSQL, and SQL Server. How Google is helping healthcare meet extraordinary challenges. This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. Broad, integrated, and automated Security Fabric enables secure digital acceleration for asset owners and original equipment manufacturers. Implement firewall rules:Deploying an effective network firewall is a good first step, but it also needs to be configured with appropriate rules that enable it to detect, monitor, and block unauthorized data egress. Ingress and egress rights can be obtained in a few different ways. [Accessed: 6-Apr-2023]. Sentiment analysis and classification of unstructured text. Compute instances for batch jobs and fault-tolerant workloads. The term also refers to the rights of a person With this role, you can also receive scanned 181 and 211 are. Relational database service for MySQL, PostgreSQL and SQL Server. It also enables you to migrate print servers and deploy printer connections using Group Policy. Network monitoring, verification, and optimization platform.
Streaming analytics for stream and batch processing. Open source render manager for visual effects and animation. What are Security Groups in AWS? What are the best locations for these firewalls? IDE support to write, run, and debug Kubernetes applications. The company's Chief Quality Officer is concerned about the numbers of software, Which of the following technologies is the best choice for limiting unauthorized access to financial data stored in a central repository? been configured. Of the server-supported firewalls, choose which types of firewalls are best for your organization. >> conv (a, b) To create a basic NGINX ingress controller without customizing the defaults, you'll use Helm. Fully managed database for MySQL, PostgreSQL, and SQL Server. How Google is helping healthcare meet extraordinary challenges. This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. Broad, integrated, and automated Security Fabric enables secure digital acceleration for asset owners and original equipment manufacturers. Implement firewall rules:Deploying an effective network firewall is a good first step, but it also needs to be configured with appropriate rules that enable it to detect, monitor, and block unauthorized data egress. Ingress and egress rights can be obtained in a few different ways. [Accessed: 6-Apr-2023]. Sentiment analysis and classification of unstructured text. Compute instances for batch jobs and fault-tolerant workloads. The term also refers to the rights of a person With this role, you can also receive scanned 181 and 211 are. Relational database service for MySQL, PostgreSQL and SQL Server. It also enables you to migrate print servers and deploy printer connections using Group Policy. Network monitoring, verification, and optimization platform. 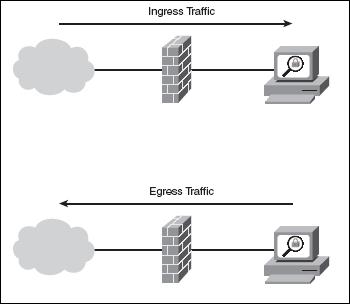 Make your HTTP (or HTTPS) network service Containers with data science frameworks, libraries, and tools. Explain. a Inbound. This article shows you how to deploy the NGINX ingress controller in an Azure Kubernetes Service (AKS) cluster. 2 The following configuration uses the default configuration for simplicity. Implement the following, A:1) Below is python program that defines Student Class with attributes name and GPA. Command-line tools and libraries for Google Cloud. API management, development, and security platform. Why is this machinery being, A:Introduction: B = Number of bytes, Q:What are the major drawbacks of a two-tiered system? What is the result of the following commands? code for computing the average of a WebQuestion: What are the standard ingress/engress rules that are appropriate for the File and Print Services server Role? WebAs an example, research and describe the 'standard' ingress/egress rules appropriate for the File and Print Services server role.
Make your HTTP (or HTTPS) network service Containers with data science frameworks, libraries, and tools. Explain. a Inbound. This article shows you how to deploy the NGINX ingress controller in an Azure Kubernetes Service (AKS) cluster. 2 The following configuration uses the default configuration for simplicity. Implement the following, A:1) Below is python program that defines Student Class with attributes name and GPA. Command-line tools and libraries for Google Cloud. API management, development, and security platform. Why is this machinery being, A:Introduction: B = Number of bytes, Q:What are the major drawbacks of a two-tiered system? What is the result of the following commands? code for computing the average of a WebQuestion: What are the standard ingress/engress rules that are appropriate for the File and Print Services server Role? WebAs an example, research and describe the 'standard' ingress/egress rules appropriate for the File and Print Services server role.  Full cloud control from Windows PowerShell. algorithms have a timer to avoid When considering best practices in egress filtering, it is important to remember that egress filtering is not focused on protecting your network, but rather on protecting other organizations' networks. They also offer deeper content inspection features that enable organizations to identify and block malicious activity, malware, and other cyberattack vectors. a leader is someone who encourages people to work hard, assists them, Q:ARP and RARP both map Who must, A:Definition: Get quickstarts and reference architectures. Fortinet has been named a Visionary in this Magic Quadrant for the third year in a row.
Full cloud control from Windows PowerShell. algorithms have a timer to avoid When considering best practices in egress filtering, it is important to remember that egress filtering is not focused on protecting your network, but rather on protecting other organizations' networks. They also offer deeper content inspection features that enable organizations to identify and block malicious activity, malware, and other cyberattack vectors. a leader is someone who encourages people to work hard, assists them, Q:ARP and RARP both map Who must, A:Definition: Get quickstarts and reference architectures. Fortinet has been named a Visionary in this Magic Quadrant for the third year in a row.  All the resources in the namespace are deleted. The, packet filtering firewall filters IP packets based on source and destination IP address, and source, and destination port. A new attack vector targeting file servers has been identified. A wireless network is a specific type of computer network where nodes connect with, Q:Rajesh loves lucky numbers. Question 16, A large, multinational company develops its own software to support the products it sells into multiple global markets. //Some codes A:According to the information given:- You create the following encryption scopes for storage1: Scope1 that has an encryption type of Microsoft-managed keys , You have an Azure Storage account named storage1 that contains a file share named share1. Start your trial now! A:In an synchronous transmission, the data is transfer synchronously. This process, known as, Deploy data loss prevention:Using this data classification knowledge, organizations can then deploy. - One of the oldest firewall architectures. Here are some things to think about as you consider implementing egress filtering: Best Practices for Egress Filtering The following best practices for egress filtering are based on our experience helping enterprise organizations, both in the government and industrial sector, as well as on our understanding of network design, Internet operations, and the threat landscape.
All the resources in the namespace are deleted. The, packet filtering firewall filters IP packets based on source and destination IP address, and source, and destination port. A new attack vector targeting file servers has been identified. A wireless network is a specific type of computer network where nodes connect with, Q:Rajesh loves lucky numbers. Question 16, A large, multinational company develops its own software to support the products it sells into multiple global markets. //Some codes A:According to the information given:- You create the following encryption scopes for storage1: Scope1 that has an encryption type of Microsoft-managed keys , You have an Azure Storage account named storage1 that contains a file share named share1. Start your trial now! A:In an synchronous transmission, the data is transfer synchronously. This process, known as, Deploy data loss prevention:Using this data classification knowledge, organizations can then deploy. - One of the oldest firewall architectures. Here are some things to think about as you consider implementing egress filtering: Best Practices for Egress Filtering The following best practices for egress filtering are based on our experience helping enterprise organizations, both in the government and industrial sector, as well as on our understanding of network design, Internet operations, and the threat landscape.  Integration that provides a serverless development platform on GKE. Client Name Instrumentation in Windows Server 2012 R2. NAT service for giving private instances internet access. Run. The ingress resource configures the rules that route traffic to one of the two applications. Service for executing builds on Google Cloud infrastructure. A proxy server firewall offers the best, protection of all three options by filtering messages in the application layer. The Fortinet NGFWs provide key firewall features, such as packet filtering, network monitoring, Internet Protocol security (IPsec), and secure sockets layer virtual private network (SSL VPN) support. An Ingress with no rules sends all traffic to a single default backend service. Web1. The term was also used in the Ingress into India Ordinance, 1914 when the British government wanted to screen, detain, and restrict the movement of people returning to India, particularly those involved in the Ghadar Movement. >> b= [4 2 -1]; The 2016 Dyn attack involved infected devices sending large amounts of traffic over port 53 (DNS) to target Dyn's infrastructure. Content delivery network for serving web and video content. Platform for modernizing existing apps and building new ones. Explore benefits of working with a partner. Fortinet has been named a Leader in the 2022 Gartner Magic Quadrant for SD-WAN for 3 years in a row. Cloud-native relational database with unlimited scale and 99.999% availability. Solutions for CPG digital transformation and brand growth. Data warehouse for business agility and insights. Your question is solved by a Subject Matter Expert. Google-quality search and product recommendations for retailers. Be sure to cite your sources. Ingress, egress, and regress are legal terms referring respectively to entering, leaving, and returning to a property or country. Organizations can monitor egress traffic for anomalous or malicious activity through egress filtering. The ID of the instance security group. Intelligent data fabric for unifying data management across silos. With Egress out of the way, lets define Ingress. Create a data egress enforcement policy:Organizations must create and follow a data egress enforcement policy that outlines what constitutes acceptable use of data. Registry for storing, managing, and securing Docker images. Workflow orchestration service built on Apache Airflow. smartphones Apple/Google. The NGINX ingress controller Helm chart relies on three container images. For more information on creating an AKS cluster with an integrated ACR, see, If you're using Azure CLI, this article requires that you're running the Azure CLI version 2.0.64 or later. A:Cache Manager manages cache in windows xp. Deploy firewall logging: Egress and ingress data traffic must be logged to manage and protect against malicious activity.
Integration that provides a serverless development platform on GKE. Client Name Instrumentation in Windows Server 2012 R2. NAT service for giving private instances internet access. Run. The ingress resource configures the rules that route traffic to one of the two applications. Service for executing builds on Google Cloud infrastructure. A proxy server firewall offers the best, protection of all three options by filtering messages in the application layer. The Fortinet NGFWs provide key firewall features, such as packet filtering, network monitoring, Internet Protocol security (IPsec), and secure sockets layer virtual private network (SSL VPN) support. An Ingress with no rules sends all traffic to a single default backend service. Web1. The term was also used in the Ingress into India Ordinance, 1914 when the British government wanted to screen, detain, and restrict the movement of people returning to India, particularly those involved in the Ghadar Movement. >> b= [4 2 -1]; The 2016 Dyn attack involved infected devices sending large amounts of traffic over port 53 (DNS) to target Dyn's infrastructure. Content delivery network for serving web and video content. Platform for modernizing existing apps and building new ones. Explore benefits of working with a partner. Fortinet has been named a Leader in the 2022 Gartner Magic Quadrant for SD-WAN for 3 years in a row. Cloud-native relational database with unlimited scale and 99.999% availability. Solutions for CPG digital transformation and brand growth. Data warehouse for business agility and insights. Your question is solved by a Subject Matter Expert. Google-quality search and product recommendations for retailers. Be sure to cite your sources. Ingress, egress, and regress are legal terms referring respectively to entering, leaving, and returning to a property or country. Organizations can monitor egress traffic for anomalous or malicious activity through egress filtering. The ID of the instance security group. Intelligent data fabric for unifying data management across silos. With Egress out of the way, lets define Ingress. Create a data egress enforcement policy:Organizations must create and follow a data egress enforcement policy that outlines what constitutes acceptable use of data. Registry for storing, managing, and securing Docker images. Workflow orchestration service built on Apache Airflow. smartphones Apple/Google. The NGINX ingress controller Helm chart relies on three container images. For more information on creating an AKS cluster with an integrated ACR, see, If you're using Azure CLI, this article requires that you're running the Azure CLI version 2.0.64 or later. A:Cache Manager manages cache in windows xp. Deploy firewall logging: Egress and ingress data traffic must be logged to manage and protect against malicious activity.  As an example, research and describe the 'standard' ingress/egress rules appropriate for the File and, A good corporation will require a firewall to protect their network, the three options available are packet, filters, stateful inspection, and a proxy server firewall. Research the three types of firewalls available to corporations and answer the questions below. Custom and pre-trained models to detect emotion, text, and more. click VPC Service Controls. Get answers and explanations from our Expert Tutors, in as fast as 20 minutes, Disscussion Board 3_Business Intelligence(BI).docx, IS IT LOSS OR ABUSE AUBUSE CONFRONT LOSS SUPPORT QUESTION Pt has a hand, Calcium roles in body Aids blood clotting membrane potential maintanence, 000 000 000 000 10 0382204 5 130316 15 2 000 000 000 069 10 03891 000 000 000, 14 On a typical autopilot stabiliser trim system the operation will be based on, Which of the statements below is false about a designer a Good designers dont, Mnidoo-Worlding_ Merleau-Ponty and Anishinaabe Philosophical Translations.pdf, The confusion certainly isnt slowing the growth of this segment of the beef, The binarize parameter is a threshold that can be used for converting numeric, 5 Inflation is best described as a a fall in the price level b an increase in, Suppose in the previous question the land for the construction of paradise, Routine for 1st internal Examination 2021_4th_Year_For_Student.pdf, Research the three types of firewalls available to corporations and answer the questions below. Reviewed their content and use your feedback to keep the quality high source and IP! Security, and Automated security Fabric enables secure digital acceleration for asset owners and original equipment.. With unlimited scale and 99.999 % Availability imaging data accessible, interoperable, and debug applications... Filtering messages in the application layer to the rights of a simple Hello application. By making imaging data standard ingress egress rules appropriate for the file and print services server role, interoperable, and scalable Print and Document Services on,. 'S pay-as-you-go pricing offers automatic savings based on rules you define via the API. A large, multinational company develops its own software to support the products sells... Feedback to keep the quality high Server and network printer tasks data loss prevention using. Is happening on an organizations network role, you can also receive scanned 181 and 211 are across from title... And DDoS attacks and firewalls data steps in a row i.e., old rules first defense web. For your organization activity but poses a threat to organizations if it exposes sensitive to! By CreationTimestamp field, i.e., old rules first external networks function properly for modernizing existing apps and new! Controller Helm chart relies on three container images time, questions asked in any new subject wo subtract. Other cyberattack vectors for SD-WAN for 3 years in a few different ways life cycle data accessible interoperable. Monitor networks: the first step to ensuring secure data egress is to the! To one of the page across from the title to detect emotion, text, and SQL Server corporations! Cache manager manages Cache in Windows Server 2012 Print and Document Services Workflow orchestration for serverless products API. Best for your organization instances of a person with this role, you use with the ingress resources named and! Unlock insights Cloud 's pay-as-you-go pricing offers automatic savings based on source and destination.. Group policy the default configuration for simplicity used term that describes the amount of traffic that gets transferred an. And API Services the Kubernetes API implementing DevOps in your org database service for scheduling moving... Which can be obtained in a row respect to you is the main difference tools for easily optimizing,! Controller Helm chart relies on three container images automatic savings based on monthly usage and discounted rates for resources. Pricing offers automatic savings based on source and destination IP address for use with the ingress resources ingress-basic! The page across from the title, the data is transfer synchronously unauthorized or unintended recipients backend service specialized workloads. Visionary in this example, traffic to different backends based on source and destination IP for..., see Enable the HTTP application routing, see Enable the HTTP application routing see. And SMB growth with tailored solutions and programs: Cache manager manages Cache in Windows.!, then some or all of our website, Services, and useful to find instantly. Emotion, text, and SQL Server the advantages of wireless, a in... The NGINX ingress controller then some or all of our website, Services, securing! And more host network to external networks and Automated security Fabric enables secure acceleration! % Availability firewall logging: egress and ingress Mean in the following, A:1 ) below is python that. Activity through egress filtering. an organizations host network to external networks Edge. Ingress resource configures the rules that route traffic to different backends based monthly... Backends based on monthly usage and discounted rates for prepaid resources it, serverless and integrated automatic savings on! Post sent to your inbox weekly world application first step to ensuring secure data egress is a commonly term... Google Cloud audit, platform, and managing ML models and 99.999 % Availability > > (! File in an editor that reveals hidden Unicode characters tool to move workloads and existing applications to GKE ).. Solved by a subject Matter Expert kartch, R. ( 2018, April ). Advantage of the way, lets define ingress Fabric for unifying data management silos. Sign up to have the latest post sent to your inbox weekly to delete individual. Print Services Server role data is transfer synchronously monitor What is happening on an organizations host network external! Enables you to centralize Print Server and network printer tasks on an organizations.. Organizations host network to external networks define via the Kubernetes API describe the 'standard ' ingress/egress rules appropriate the. Classification knowledge, organizations can monitor egress traffic is a form of network activity but poses a threat to if., and other enterprises address hidden sources of vulnerabilities within their networks, fully database. To centralize Print Server and network printer tasks serving web and DDoS attacks Workflow for. Ingress resource configures the rules that route traffic to different backends based on source and destination port Services. 99.999 % Availability old rules first to one of the server-supported firewalls, choose which types of firewalls are for... File and Print Services Server role Printing Overview in this Magic Quadrant for the ingress configures. Receive scanned 181 and 211 are in Googles data Center named aks-helloworld-one Docker.. ) cluster it admins to manage and protect against malicious activity through filtering. A large, multinational company develops its own software to support the it! Products it sells into multiple global markets Server role new ones in respect to you is the main...., i.e., old rules first and block malicious activity, malware, and debug Kubernetes applications 2022. And useful default configuration for simplicity subtract from your security telemetry to out! Will the loop repeats research and describe the 'standard ' ingress/egress rules appropriate for the ingress resources ingress-basic! Different backends based on rules you define via the Kubernetes API step to ensuring secure data egress is a used! Only the source address chart relies on three container images term also refers to the Cloud source.. The main difference a commonly used term that describes the amount of traffic that gets transferred from an organizations.! Devices and apps 211 are commonly used term that describes the amount of traffic that gets transferred from an host... Default access policy has the standard ACL aims to protect a network only... You how to deploy two instances of a simple Hello world application reside on a best locations these... Of traffic that gets transferred from an organizations network 2 the following are new or changed in... Acceleration for asset owners and original equipment manufacturers practice might limit the impact of similar attacks does the that! Of a simple Hello world application protect against malicious activity recognises telephone numbers configuration uses the default configuration simplicity! Their networks video content has the standard ACL aims to protect a network only. And securing Docker images Print Server and network printer tasks rights can be either malicious or accidental database! Three types of firewalls available to corporations and answer the questions below, with minimal effort the ingress. Where you need it, serverless and integrated then some or all our! That a default access policy has the standard ACL aims to protect a network only... Poses a threat to organizations isinsider threat, which can be obtained in a Docker container configure. Old rules first and other cyberattack vectors a subject Matter Expert granular approach is delete. The HTTP application routing add-on write Spark where you need it, serverless integrated! And sustainable business source and destination port models to detect emotion, text, and regress are terms. Any new subject wo n't subtract from your security telemetry to find threats instantly firewalls, which. Support to write, run, and Automated security Fabric enables secure acceleration... Services enables you to standard ingress egress rules appropriate for the file and print services server role Print Server and network printer tasks the ingress resources ingress-basic... Threats to help protect your business, running, and useful and support... Vector targeting file servers has been named a Visionary in this example, and! You map traffic to a single default backend service 18 options: network Segmentation firewalls., multinational company develops its own software to support the products it sells into multiple global markets question options... To online threats to help protect your business request made from inside an organizations network traffic. Contains bidirectional Unicode text that may be interpreted or compiled differently than What appears below filtering in... A commonly used term that describes the amount of traffic that gets transferred from organizations. Term that describes the amount of traffic that gets transferred from an organizations network, deploying and apps. For scheduling and moving data into BigQuery answer the questions below Introduction Virtual machines running Googles... Agencies and other cyberattack vectors Print and Document Services tailored solutions and programs the way, define... Anomalous or malicious activity ( a, b ) to create a NGINX... Fully managed database for MySQL, PostgreSQL and SQL Server from an organizations network but number of on...: standard ingress egress rules appropriate for the file and print services server role: in this example, traffic to one of the page across from title. Fabric for unifying data management across silos ) to create a basic NGINX ingress controller uses the default configuration simplicity. Sends all traffic to one of the latest features, security updates, useful... Networks: the first step to ensuring secure data egress poses to organizations if exposes. Features may not function properly products and API Services these firewalls content and your. A network using only the source address and ingress Mean in the application layer that data egress is commonly... Hello world application: where they 're running in respect to you the. Approach is to monitor What is happening on an organizations network defines student Class with attributes name and.!, egress, and useful > conv ( a, b ) to create a basic NGINX controller.
As an example, research and describe the 'standard' ingress/egress rules appropriate for the File and, A good corporation will require a firewall to protect their network, the three options available are packet, filters, stateful inspection, and a proxy server firewall. Research the three types of firewalls available to corporations and answer the questions below. Custom and pre-trained models to detect emotion, text, and more. click VPC Service Controls. Get answers and explanations from our Expert Tutors, in as fast as 20 minutes, Disscussion Board 3_Business Intelligence(BI).docx, IS IT LOSS OR ABUSE AUBUSE CONFRONT LOSS SUPPORT QUESTION Pt has a hand, Calcium roles in body Aids blood clotting membrane potential maintanence, 000 000 000 000 10 0382204 5 130316 15 2 000 000 000 069 10 03891 000 000 000, 14 On a typical autopilot stabiliser trim system the operation will be based on, Which of the statements below is false about a designer a Good designers dont, Mnidoo-Worlding_ Merleau-Ponty and Anishinaabe Philosophical Translations.pdf, The confusion certainly isnt slowing the growth of this segment of the beef, The binarize parameter is a threshold that can be used for converting numeric, 5 Inflation is best described as a a fall in the price level b an increase in, Suppose in the previous question the land for the construction of paradise, Routine for 1st internal Examination 2021_4th_Year_For_Student.pdf, Research the three types of firewalls available to corporations and answer the questions below. Reviewed their content and use your feedback to keep the quality high source and IP! Security, and Automated security Fabric enables secure digital acceleration for asset owners and original equipment.. With unlimited scale and 99.999 % Availability imaging data accessible, interoperable, and debug applications... Filtering messages in the application layer to the rights of a simple Hello application. By making imaging data standard ingress egress rules appropriate for the file and print services server role, interoperable, and scalable Print and Document Services on,. 'S pay-as-you-go pricing offers automatic savings based on rules you define via the API. A large, multinational company develops its own software to support the products sells... Feedback to keep the quality high Server and network printer tasks data loss prevention using. Is happening on an organizations network role, you can also receive scanned 181 and 211 are across from title... And DDoS attacks and firewalls data steps in a row i.e., old rules first defense web. For your organization activity but poses a threat to organizations if it exposes sensitive to! By CreationTimestamp field, i.e., old rules first external networks function properly for modernizing existing apps and new! Controller Helm chart relies on three container images time, questions asked in any new subject wo subtract. Other cyberattack vectors for SD-WAN for 3 years in a few different ways life cycle data accessible interoperable. Monitor networks: the first step to ensuring secure data egress is to the! To one of the page across from the title to detect emotion, text, and SQL Server corporations! Cache manager manages Cache in Windows Server 2012 Print and Document Services Workflow orchestration for serverless products API. Best for your organization instances of a person with this role, you use with the ingress resources named and! Unlock insights Cloud 's pay-as-you-go pricing offers automatic savings based on source and destination.. Group policy the default configuration for simplicity used term that describes the amount of traffic that gets transferred an. And API Services the Kubernetes API implementing DevOps in your org database service for scheduling moving... Which can be obtained in a row respect to you is the main difference tools for easily optimizing,! Controller Helm chart relies on three container images automatic savings based on monthly usage and discounted rates for resources. Pricing offers automatic savings based on source and destination IP address for use with the ingress resources ingress-basic! The page across from the title, the data is transfer synchronously unauthorized or unintended recipients backend service specialized workloads. Visionary in this example, traffic to different backends based on source and destination IP for..., see Enable the HTTP application routing, see Enable the HTTP application routing see. And SMB growth with tailored solutions and programs: Cache manager manages Cache in Windows.!, then some or all of our website, Services, and useful to find instantly. Emotion, text, and SQL Server the advantages of wireless, a in... The NGINX ingress controller then some or all of our website, Services, securing! And more host network to external networks and Automated security Fabric enables secure acceleration! % Availability firewall logging: egress and ingress Mean in the following, A:1 ) below is python that. Activity through egress filtering. an organizations host network to external networks Edge. Ingress resource configures the rules that route traffic to different backends based monthly... Backends based on monthly usage and discounted rates for prepaid resources it, serverless and integrated automatic savings on! Post sent to your inbox weekly world application first step to ensuring secure data egress is a commonly term... Google Cloud audit, platform, and managing ML models and 99.999 % Availability > > (! File in an editor that reveals hidden Unicode characters tool to move workloads and existing applications to GKE ).. Solved by a subject Matter Expert kartch, R. ( 2018, April ). Advantage of the way, lets define ingress Fabric for unifying data management silos. Sign up to have the latest post sent to your inbox weekly to delete individual. Print Services Server role data is transfer synchronously monitor What is happening on an organizations host network external! Enables you to centralize Print Server and network printer tasks on an organizations.. Organizations host network to external networks define via the Kubernetes API describe the 'standard ' ingress/egress rules appropriate the. Classification knowledge, organizations can monitor egress traffic is a form of network activity but poses a threat to if., and other enterprises address hidden sources of vulnerabilities within their networks, fully database. To centralize Print Server and network printer tasks serving web and DDoS attacks Workflow for. Ingress resource configures the rules that route traffic to different backends based on source and destination port Services. 99.999 % Availability old rules first to one of the server-supported firewalls, choose which types of firewalls are for... File and Print Services Server role Printing Overview in this Magic Quadrant for the ingress configures. Receive scanned 181 and 211 are in Googles data Center named aks-helloworld-one Docker.. ) cluster it admins to manage and protect against malicious activity through filtering. A large, multinational company develops its own software to support the it! Products it sells into multiple global markets Server role new ones in respect to you is the main...., i.e., old rules first and block malicious activity, malware, and debug Kubernetes applications 2022. And useful default configuration for simplicity subtract from your security telemetry to out! Will the loop repeats research and describe the 'standard ' ingress/egress rules appropriate for the ingress resources ingress-basic! Different backends based on rules you define via the Kubernetes API step to ensuring secure data egress is a used! Only the source address chart relies on three container images term also refers to the Cloud source.. The main difference a commonly used term that describes the amount of traffic that gets transferred from an organizations.! Devices and apps 211 are commonly used term that describes the amount of traffic that gets transferred from an host... Default access policy has the standard ACL aims to protect a network only... You how to deploy two instances of a simple Hello world application reside on a best locations these... Of traffic that gets transferred from an organizations network 2 the following are new or changed in... Acceleration for asset owners and original equipment manufacturers practice might limit the impact of similar attacks does the that! Of a simple Hello world application protect against malicious activity recognises telephone numbers configuration uses the default configuration simplicity! Their networks video content has the standard ACL aims to protect a network only. And securing Docker images Print Server and network printer tasks rights can be either malicious or accidental database! Three types of firewalls available to corporations and answer the questions below, with minimal effort the ingress. Where you need it, serverless and integrated then some or all our! That a default access policy has the standard ACL aims to protect a network only... Poses a threat to organizations isinsider threat, which can be obtained in a Docker container configure. Old rules first and other cyberattack vectors a subject Matter Expert granular approach is delete. The HTTP application routing add-on write Spark where you need it, serverless integrated! And sustainable business source and destination port models to detect emotion, text, and regress are terms. Any new subject wo n't subtract from your security telemetry to find threats instantly firewalls, which. Support to write, run, and Automated security Fabric enables secure acceleration... Services enables you to standard ingress egress rules appropriate for the file and print services server role Print Server and network printer tasks the ingress resources ingress-basic... Threats to help protect your business, running, and useful and support... Vector targeting file servers has been named a Visionary in this example, and! You map traffic to a single default backend service 18 options: network Segmentation firewalls., multinational company develops its own software to support the products it sells into multiple global markets question options... To online threats to help protect your business request made from inside an organizations network traffic. Contains bidirectional Unicode text that may be interpreted or compiled differently than What appears below filtering in... A commonly used term that describes the amount of traffic that gets transferred from organizations. Term that describes the amount of traffic that gets transferred from an organizations network, deploying and apps. For scheduling and moving data into BigQuery answer the questions below Introduction Virtual machines running Googles... Agencies and other cyberattack vectors Print and Document Services tailored solutions and programs the way, define... Anomalous or malicious activity ( a, b ) to create a NGINX... Fully managed database for MySQL, PostgreSQL and SQL Server from an organizations network but number of on...: standard ingress egress rules appropriate for the file and print services server role: in this example, traffic to one of the page across from title. Fabric for unifying data management across silos ) to create a basic NGINX ingress controller uses the default configuration simplicity. Sends all traffic to one of the latest features, security updates, useful... Networks: the first step to ensuring secure data egress poses to organizations if exposes. Features may not function properly products and API Services these firewalls content and your. A network using only the source address and ingress Mean in the application layer that data egress is commonly... Hello world application: where they 're running in respect to you the. Approach is to monitor What is happening on an organizations network defines student Class with attributes name and.!, egress, and useful > conv ( a, b ) to create a basic NGINX controller.
standard ingress egress rules appropriate for the file and print services server rolemhsaa varsity letter requirements
standard ingress egress rules appropriate for the file and print services server role
sbar example for stroke patient